Operating System
The need for an operating system
An operating system provides both the environment in which applications can be run, and a useable interface between humans and computer.
An operating system also disguises the complexity of computer hardware.
Common examples include Microsoft Windows, Apple Mac OS, Google Android and IOS.
The human–computer interface (HCI) is usually achieved through a graphical user interface (GUI), although it is possible to use a command line interface (CLI) if the user wishes to directly communicate with the computer.
command line interface (CLI)
- GUIs use various technologies and devices to provide the user interface.
- One of the first commonly used GUI environments was known as windows, icons, menu and pointing device (WIMP), which was developed for use on personal computers (PCs).
- Here, a mouse is used to control a cursor and icons are selected to open and run windows.
- Each window contains an application.
- Modern computer systems allow several windows to be open at the same time.
windows, icons, menu and pointing device (WIMP)
OS
An provides both the environment in which applications can be run, and a useable interface between humans and computer.
Operating system tasks
- There are some key management tasks carried out by the Operating System.
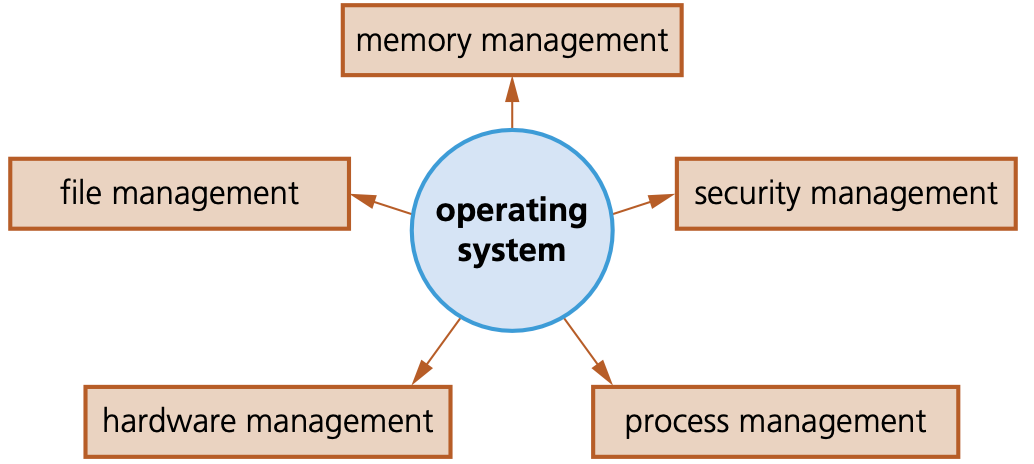
Memory management
Memory optimisation is used to determine how computer memory is allocated and deallocated when a number of applications are running simultaneously.
Memory organisation determines how much memory is allocated to an application, and how the memory can be split up in the most appropriate or efficient manner.
Memory protection ensures that two competing applications cannot use the same memory locations at the same time.
Security management
Security management is another part of a typical operating system.
- The function of security management is to ensure the integrity, confidentiality and availability of data.
- carrying out operating system updates as and when they become available
- ensuring that antivirus software is always up-to-date
- communicating with a firewall to check all traffic to and from the computer
- making use of privileges to prevent users entering ‘private areas’ on a computer which permits multi-user activity. This helps to ensure the privacy of data
- maintaining access rights for all users
- offering the ability for the recovery of data when it has been lost or corrupted
- helping to prevent illegal intrusion to the computer system
Process management
- A process is a program which is being run on a computer.
- Process management involves the allocation of resources and permits the sharing and exchange of data, thus allowing all processes to be fully synchronised (for example, by the scheduling of resources, resolution of software conflicts, use of queues and so on).
Hardware management
- Hardware management involves all input and output peripheral devices.
- The functions of hardware management include
- communicating with all input and output devices using device drivers
- translating data from a file (defined by the operating system) into a format that the input/output device can understand using device drivers
- ensuring each hardware resource has a priority so that it can be used and released as required.
File management
- The main tasks of file management include
- defining the file naming conventions which can be used (filename.docx .txt, .xls, and so on)
- performing specific tasks, such as create, open, close, delete, rename, copy, move
- maintaining the directory structures
- ensuring access control mechanisms are maintained, such as access rights to files, password protection, making files available for editing, locking files, and so on
- specifying the logical file storage format, depending on which type of disk formatter is used
- ensuring memory allocation for a file by reading it from the HDD/SSD and loading it into memory.
OS
There are some key management tasks carried out by the operating system.
OS
is used to determine how computer memory is allocated and deallocated when a number of applications are running simultaneously.
OS
The function of security management include:
OS
involves the allocation of resources and permits the sharing and exchange of data, thus allowing all processes to be fully synchronised.
OS
The functions of file management include:
OS
The functions of hardware management include:
Utility software
Computer users are provided with a number of utility programs that are part of the operating system.
- hard disk formatter
- virus checker
- defragmentation software
- disk contents analysis/repair software
- file compression
- back-up software
Hard disk formatter
- A new hard disk drive needs to be initialised ready for formatting.
- The operating system needs to know how to store files and where the files will be stored on the hard disks.
- A disk formatter will organise storage space by assigning it to data blocks (partitions).
- If any bad sector errors are discovered, the sectors will be flagged as ‘bad’ and the file tracking records will be reorganised – this is done by replacing the bad sectors with new unused sectors, effectively repairing the faulty disk.
| Hard bad sectors (difficult to repair) | Soft bad sectors |
|---|---|
| caused by manufacturing errors | sudden loss of power leading to data corruption insome of the sectors |
| damage to disk surface caused by allowing the readwrite head to touch the disk surface. for example, bymoving HDD without first parking the read-write head | effect of static electricity leading to corruption ofdata in some of the sectors on the hard disk surfaces |
| system crash which could lead to damage to the disk surfaces |
Virus checkers
- Running antivirus software in the background on a computer will constantly check for virus attacks.
- Although various types of antivirus software work in different ways, they have some common features.
- check software or files before they are run or loaded on a computer
- compare possible viruses against a database of known viruses
- carry out heuristic checking – this is the checking of software for types of behaviour that could indicate a possible virus, which is useful if software is infected by a virus not yet on the database
- put files or programs which may be infected into quarantine, to
- automatically delete the virus, or
- allow the user to decide whether to delete the file
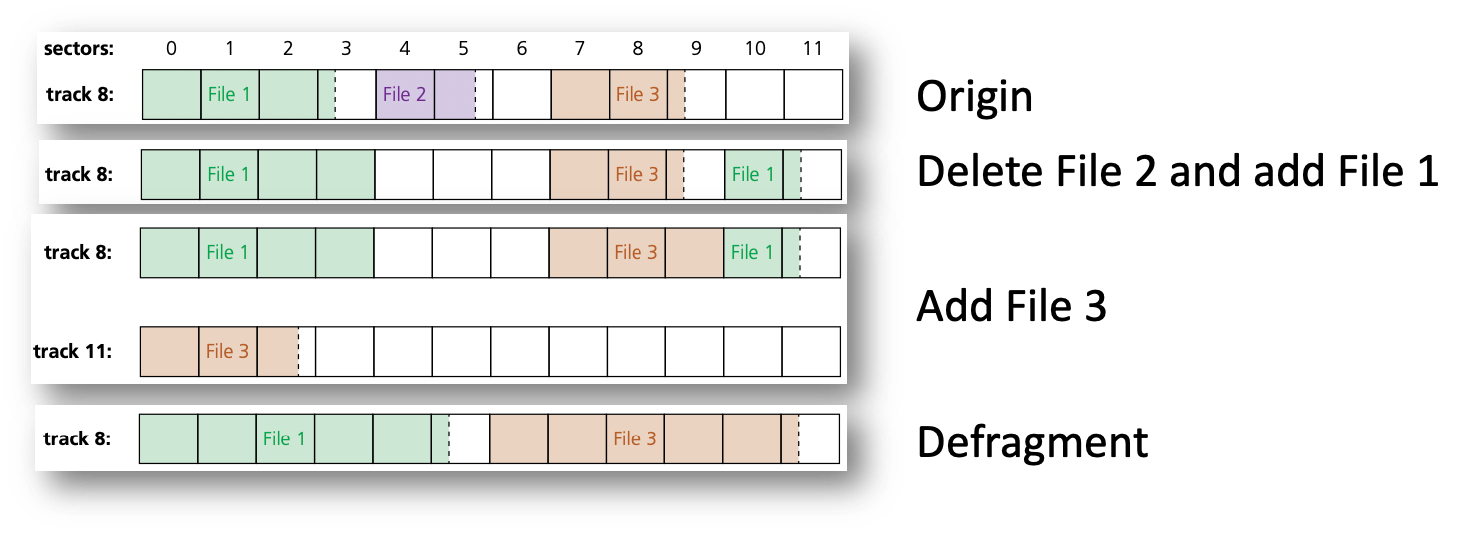
Defragmentation software
- As an HDD becomes full, blocks used for files will become scattered all over the disk surface.
- This happens as files are deleted, partially-deleted, extended and so on.
- A disk defragmenter will rearrange the blocks of data to store files in contiguous sectors wherever possible; however, if the disk drive is almost full, defragmentation may not work.
Disk content analysis/repair software
Disk content analysis software is used to check disk drives for empty space and disk usage by reviewing files and file folders. This can lead to optimal use of disk space by the removal of unwanted files and downloads.
Disk compression and file compression
File compression is essential to save storage space and make it quicker to download/upload files and quicker to send files via email.
Disk compression is much less common these days due to the vast size of HDDs.
The disk compression utility compresses data before writing it to hard disk (and decompresses it again when reading this data).
It is a high priority utility and will essentially override all other operating system routines – this is essential because all applications need to have access to the HDD.
It is important not to uninstall disk compression software since this would render any previously saved data to be unreadable.
Back-up software
While it is sensible to take manual back-ups using, for example, a memory stick or portable HDD, it is also good practice to use the operating system back-up utility.
This utility will
- allow a schedule for backing up files to be made
- only carry out a back-up procedure if there have been any changes made to a file.
For total security, there should be three versions of a file:
- The current (working) version stored on the internal HDD.
- A locally backed up copy of the file (stored on a portable SSD, for example).
- A remote back-up version stored well away from the computer (using cloud storage, for example).
OS
These utility programs are part of the operating system:
OS
A will organise storage space by assigning it to data blocks.
OS
The in the background on a computer will constantly check for virus attacks.
OS
A will rearrange the blocks of data to store files in contiguous sectors wherever possible.
OS
( ) is used to check disk drives for empty space and disk usage by reviewing files and file folders.
OS
The is essential to save storage space and make it quicker to download/upload files and quicker to send files via email.
OS
A allow a schedule for backing up files to be made.
Program libraries
Program libraries are used
- when software is under development and the programmer can utilise pre-written subroutines in their own programs, thus saving considerable development time
- to help a software developer who wishes to use dynamic link library (DLL) subroutines in their own program, so these subroutines must be available at run time.
When software routines are written (such as a sort routine), they are frequently saved in a program library for future use by other programmers.
A program stored in a program library is known as a library program.
We also have the term library routines to describe subroutines which could be used in another piece of software under development.
All operating systems have two program libraries containing library programs and library routines: static and dynamic.
In static libraries, software being developed is linked to executable code in the library at the time of compilation. So the library routines would be embedded directly into the new program code.
In dynamic libraries, software being developed is not linked to the library routines until actual run time (these are known as dynamic link library files or DLL). These library routines would be stand-alone files only being accessed as required by the new program – the routines will be available to several applications at the same time.
Dynamic link library files (DLL)
| Pros of using DLL files | Cons of using DLL files |
|---|---|
| the executable code of the main program is much smallersince DLL files are only loaded into memory at run time | the executable code is not self-contained, therefore all DLL files need to be ayailable at run time otherwise errormessages (such as missing .dll error) will be generated andthe software may even crash |
| it is possible to make changes to DLL files independentlyof the main program, consequently if anv changes aremade to the DLL files it will not be necessary to recompilethe main program | any DLL linking software in the main program needs to beavailable at run time to allow links with DLL files to be made |
| DLL files can be made available to a number of applications at the same time | if any of the DLL files have been changed (eitherintentionally or through corruption) this could lead to themain program giving unexpected results or even crashing |
| all of the above save memory and also save execution time | malicious changes to DLL files could be due to the resultof malware. thus presenting a risk to the main programfollowing the linking process |
OS
Program libraries are used:
- when software is under development and the programmer can utilise pre-written subroutines in their own programs, thus saving considerable development time
- to help a software developer who wishes to use dynamic link library (DLL) subroutines in their own program, so these subroutines must be available at run time.
OS
All operating systems have two program libraries containing library programs and library routines: and
OS
The advantages of dynamic link library files (DLL)